Professional penetration testing
Hand on heart:
How secure are your applications, networks and infrastructures?
What are the consequences of a data leak?
Find out with our professional penetration testing!
Our services for you
Six steps to success: Level up your protection
Offer
The examination mode and scope are set? Then you will receive a non-binding offer tailored to your needs.
Examination
During the entire procedure, we are in close contact with you in order to be able to react quickly to any critical findings. You speak directly to our experts.
Next steps
Successful cyber resilience begins where the classic pentest leaves off: together, we develop an advanced concept to increase your resilience against cyber attacks.
Contact
Tell us about your concerns and we will find a tailor-made solution in a joint, free initial consultation. Contact us now.
Preparation phase
A smooth implementation requires a well-thought-out plan, as well as the involvement of stakeholders and those responsible for your IT.
Final Report
Detailed descriptions of the attacks carried out and the vulnerabilities found are good, but clear and comprehensible recommendations for action are better. We offer both.
Peace of mind
for you:
Benefits of penetration testing
Increased trustworthiness and optimized market positioning as a security-conscious company
Sustainable increase in cyber resilience to prevent damage and minimize risks
Determine the real potential of damage
One step ahead of hackers
Ventum Penetration Testing:
Your Security Advantage.
Pure vulnerability scans look for already publicly known vulnerabilities on systems, in applications and IT infrastructure. These can be default passwords, common misconfigurations, or generic issues. However, highly critical risks are considered without context and get lost in hundreds or even thousands of pages of reports. And that’s with an IT department that’s probably already working at full capacity anyway.
With us as your partner, you and your IT staff benefit from the years of experience of our pentesters. Extensive automated tests based on the latest data, supplemented by our latest findings, are an important component from our penetration testing process. Through contextual consideration, as well as in-depth, manual tests, we determine which findings represent real security risks to your company.
Therefore, we design the implementation for you so transparently that you have the possibility to expand or adjust the scope of the test at any time. Fair and equally transparent billing for our services is a matter of course for us.
Verification of the findings and
contextual consideration
Purely automated
Vulnerability Scans
Ventum
Penetration Testing
Determination of the actual
attack and damage potential
Purely automated
Vulnerability Scans
Ventum
Penetration Testing
Check for
combined vulnerabilities
Purely automated
Vulnerability Scans
Ventum
Penetration Testing
Standardized targets, publicly
known and generic gaps
Purely automated
Vulnerability Scans
Ventum
Penetration Testing
In-depth testing incl. Analysis of
proprietary, undocumented
protocols, data formats, services
Purely automated
Vulnerability Scans
Ventum
Penetration Testing
Detection of problems
through security-by-obscurity
Purely automated
Vulnerability Scans
(only publicly known)
Ventum
Penetration Testing
Purely automated vulnerability scans
Verification of findings and context-based analysis
Help to identify real attack and damage potential
Checking for combined vulnerabilities and threats
Standardised targets, publicly known or generic vulnerablities
In-depth analysis incl. proprietary, non-generic protocols, data formats and services
Detection of problems through security-by-obscurity
(only publicly known)
Ventum
Penetration Testing
Knowledge, experience, combinatorics, contextual consideration
low criticality
high criticality
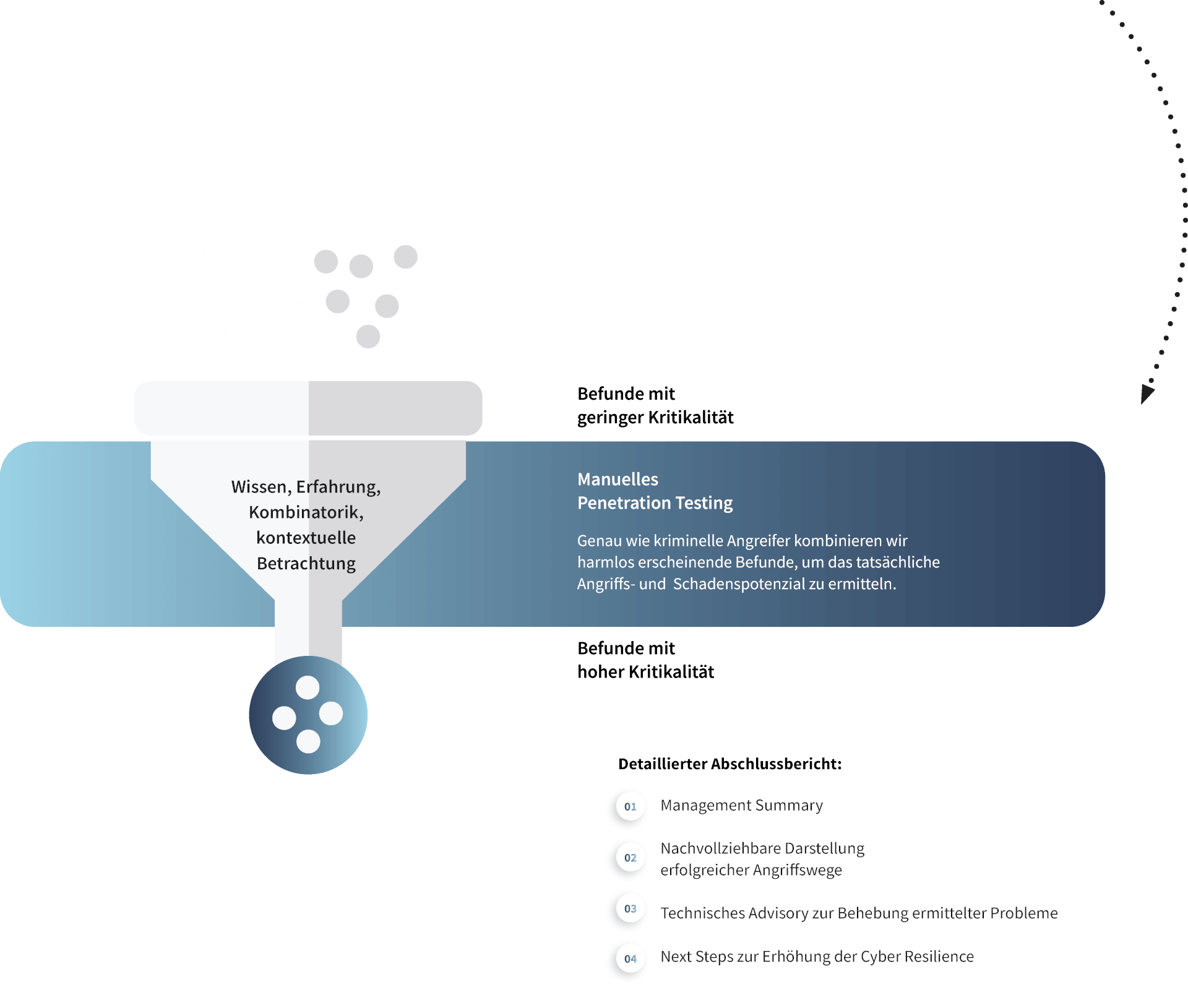
What does a pentest cost?
The effort of a penetration test depends on the scope and the required test depth. Talk to us and you will receive a personal fixed-price offer based on your scope and examination modalities, usually on the next working day.
Why Ventum Consulting for penetration testing?
Manual instead of purely automated: Combinatorics, knowledge and experience instead of contextless findings
Concrete, comprehensible recommendations for your company and optional implementation support
Our work is not done after submitting the report
We do not only suggest measures, but also support their implementation
Ventum Value Proposition
No set patterns
Transparency
Sustainable
Personal
- Ventum Consulting Penetration Testing
Your Security Advantage.
Daniel Querzola
Daniel’s background is in deep technical areas such as pentesting and vulnerability management. He combines his technical security know-how with a strategic solution-oriented approach to contribute significantly to the cyber resilience of his customers.
His core expertise includes deep-dive pentesting in the context of complex enterprise architectures, as well as vulnerability management of web applications.


Michael Niewöhner
Michael is an expert in the IT security environment. With years of experience in penetration testing and reverse engineering, he has deep and broad technical expertise.
Thanks to his hacker mentality and strong analytical mindset, he solves problems in unconventional ways and contributes significantly to his clients’ cyber resilience from an attacker’s perspective.
Frequently asked questions
A penetration test – pentest for short – is a in-depth examination of software, hardware or a complete IT infrastructure for weak points. These can serve as gateways for criminal hackers to access sensitive data such as trade secrets or to cause targeted damage through manipulation. The best protection against this is to take the attacker’s perspective. For this reason, the techniques of real attackers are used in a penetration test – without causing damage of course.
Every exam is different. Depending on the scope, complexity and approach, the implementation time varies. That’s why our experienced inspectors work with you to develop an economically viable inspection scenario – perfectly tailored to your requirements. Request your non-binding offer now.
Our experts examine your IT infrastructure or product from the perspective of a real attacker and also apply their techniques. In doing so, they uncover vulnerabilities that would otherwise remain hidden, helping you strengthen your resilience against cyberattacks.
IT architectures are primarily designed to function, while security is a secondary priority. Too often, the standard configuration specified by manufacturers is relied on, which is usually anything but secure. These problems are often only discovered after the damage has already occurred. A penetration reveals them to you before a real attacker takes the chance.
Attackers typically take weeks or months to prepare before the actual attack takes place. The whitebox approach deliberately skips this preparation phase by reviewing source code, documentation, network diagrams, and so on. This procedure is suitable for obtaining as much information as possible about the security status of the environment or application in as short a time as possible. This saves you time and money.
We like to grope in the dark so you don’t have to! In contrast to the whitebox approach, the auditors have as little information as possible at their disposal. This enables a realistic estimate of how long it would take an attacker to extract data or cause damage. This approach is useful to evaluate the effectiveness of the protective measures in an already secured environment under real conditions. The disadvantage here: the time of conduct is significantly longer than in a whitebox procedure.
Black + White = Grey. The greybox penetration test combines the advantages of blackbox and whitebox approaches. Depending on the objective of the test, any gradation of the level of information is possible. Therefore, our pentesters recommend a dynamic approach: first, only general information is provided. Specific information is only requested on a case-by-case basis during the course of the audits. This makes it possible to create a scenario that is as realistic as possible. This is easier on the wallet than the pure black box approach. Keyword: cost efficiency.
Malware scanners and firewalls generally only protect against known threats or threats that can be detected based on behavior. The penetration test, on the other hand, reveals generic weaknesses such as misconfigurations, insecure standard configurations or planning errors. It is also checked whether existing protective measures are working correctly.
Security appliances and endpoint protection are important components of cyber defense – that is undeniable. The penetration test evaluates the effectiveness of these and other protective measures in the overall context of the infrastructure in order to sharpen them further. Better be safe than sorry.
Our motto: Right Tool for the Job. A list of tools would therefore make little sense at this point, because: it is not the camera that makes the photo, but the photographer. Our penetration testers use a variety of tools and scripts, from open source tools to homegrown zero-day exploits. Secret technology does not exist. This gives you deep insight into the attacker’s world at any time.
Contact us now!
Uncover and mitigate your vulnerabilities with Ventum.
